

CONTENTS
FOREWORD …………………………………………………….. 4
TASK DISTRIBUTION ……………………………………….. 6
TIPS TO HELP STOP CYBERBULLYING ………………. 8
PASSWORDS ………………………………………………….. 18
SOCIAL ENGINEERING ……………………………………. 20
RISKY ONLINE BEHAVIORS ……………………………. 24
DIGITAL RIGHTS AND DIGITAL CITIZENSHIP ……..32
BACKUPS…………………………………………………………. 38
TIPS OF PARENTS WITH TEENAGERS ……………….. 40
HIDDEN DANGERS IN SOCIAL NETWORKS AND HOW TO USE IT SAFELY ……………………………………………………………. 44
FORMS OF CYBER BULLYİNG …………………………… 48
PHISHING ………………………………………………………… 56
DIGITAL FOOTPRINT ………………………………………….58
CAUTIONS …………………………………………………………60
QR CODE …………………………………………………………..66

“GET CYBER SKILLED and PREVENT CYBERBULLIYING”
PROJECT FINAL PRODUCT
Individuals are surrounded by new threats with the ncrease of internet usage in a world that is rapidly digitalizing. Online crimes such as theft, fraud, terrorism, cyberbullying are increasing day by day.
Today’s students have grown up online, so they have to been told the basics, such as creating strong passwords and protecting personal information. However, they may not understand why. By explaining how hackers obtain passwords and other information, it will help students understand the importance of this basic security skill. Additionally, students should be taught how to deal with cyber bullies By going through the basics and showing real-life examples of how cyber crimes hurt, students will have a better grasp of cyber security.
Our project is aimed enable students to get cyber skilled and to make aware of online threats and help to prevent cyberbullying by increasing their awareness and competence on cyber security. Pupils who acquire these skills will be able to protect themselves from cyber crimes and cyberbullying Thus, they will be able to make new discoveries and produce new products by using technology and internet more effectively.
As a final product, we prepared this guide book on cyber security and cyberbullying to enhance the sustainability of our project. After sharing topics between partner schools, the project students researched as a team and agreed with the project teacher on the information they wanted to include in the book. This prepared guide book will be uploaded to the website of each project partner school and blog of the project. Hereby it can reach and be available to more people.
PROJECT FOUNDERS
FİLİZ ŞEN & VIRGINIE MATHIEU


TIPS TO HELP STOP CYBERBULLYING
Keşan Ticaret ve Sanayi Odası MTAL (Filiz Şen)
For kids and teens
Know that it’s not your fault. What people call “bullying” is sometimes an argument between two people. But if someone is repeatedly cruel to you, that’s bullying and you mustn’t blame yourself. No one deserves to be treated cruelly.
Don’t respond or retaliate. Sometimes a reaction is exactly what aggressors are looking for because they think it gives them power over you, and you don’t want to empower a bully. As for retaliating, getting back at a bully turns you into one – and can turn one mean act into a chain reaction. If you can, remove yourself from the situation. If you can’t, sometimes humor disarms or distracts a person from bullying.
Save the evidence. The only good news about bullying online or on phones is that it can usually be captured, saved, and shown to someone who can help. You can save that evidence in case things escalate.
Tell the person to stop. This is completely up to you – don’t do it if you don’t feel totally comfortable doing it, because you need to make your position completely clear that you will not stand for this treatment any more. You may need to practice beforehand with someone you trust, like a parent or good friend.
Reach out for help – especially if the behavior’s really getting to you. You deserve backup. See if there’s someone who can listen, help you process what’s going on and work through it – a friend, relative or maybe an adult you trust.

Use available tech tools. Most social media apps and services allow you to block the person. Whether the harassment’s in an app, texting, comments or tagged photos, do yourself a favor and block the person. You can also report the problem to the service. That probably won’t end it, but you don’t need the harassment in your face, and you’ll be less tempted to respond. If you’re getting threats of physical harm, you should call your local police (with a parent or guardian’s help) and consider reporting it to school authorities.
Protect your accounts. Don’t share your passwords with anyone – even your closest friends, who may not be close forever – and password-protect your phone so no one can use it to impersonate you.
If someone you know is being bullied, take action. Just standing by can empower an aggressor and does nothing to help. The best thing you can do is try to stop the bullying by taking a stand against it. If you can’t stop it, support the person being bullied. If the person’s a friend, you can listen and see how to help. Consider together whether you should report the bullying. If you’re not already friends, even a kind word can help reduce the pain. At the very least, help by not passing along a mean message and not giving positive attention to the person doing the bullying.

Additional advice for parents
Know that you’re lucky if your child asks for help. Most young people don’t tell their open-heartedly as possible. Feel free to ask if it has anything to do with mean behavior or social issues. But even if it does, don’t assume it’s bullying. You won’t know until you get the full story, starting with your child’s perspective.
Work with your child. There are two reasons why you’ll want to keep your child involved. Bullying and cyberbullying usually involve a loss of dignity or control over a social situation, and involving your child in finding solutions helps him or her regain that. The second reason is about context. Because the bullying is almost always related to school life and our kids understand the situation and context better than parents ever can, their perspective is key to getting to the bottom of the situation and working out a solution. You may need to have private conversations with others, but let your child know if you do, and report back. This is about your child’s life, so your child needs to be part of the solution.
Respond thoughtfully, not fast. What parents don’t always know is that they can make things worse for their kids if they act rashly. A lot of cyberbullying involves somebody getting marginalized (put down and excluded), which the bully thinks increases his or her power or status. If you respond publicly or if your child’s peers find out about even a discreet meeting with school authorities, the marginalization can get worse, which is why any response needs to be well thought out.
More than one perspective needed. Your child’s account of what happened is likely completely sincere, but remember that one person’s truth isn’t necessarily everybody’s. You’ll need to get other perspectives and be open-minded about what they are. Sometimes kids let themselves get pulled into chain reactions, and often what we see online is only one side of or part of the story.

What victims say helps most is to be heard – really listened to – either by a friend or an adult who cares. That’s why, if your kids come to you for help, it’s so important to respond thoughtfully and involve them. Just by being heard respectfully, a child is often well on the way to healing.
The ultimate goal is restored self-respect and greater resilience in your child. This, not getting someone punished, is the best focus for resolving the problem and helping your child heal. What your child needs most is to regain a sense of dignity. Sometimes that means standing up to the bully, sometimes not. Together, you and your child can figure out how to get there.
One positive outcome we don’t often think about (or hear in the news) is resilience. We know the human race will never completely eradicate meanness or cruelty, and we also know that bullying is not, as heard in past generations, “normal” or a rite of passage. We need to keep working to eradicate it. But when it does happen and we overcome it – our resilience grows. It’s not something that can be “downloaded” or taught. We grow it through exposure to challenges and figuring out how to deal with them. So sometimes it’s important to give them space to do that and let them know we have their back.



PASSWORDS
Babaeski Şehit Ersan Yenici AL. (Oya Arslan)
With the introduction of technology and the internet into our lives, the number of passwords we use has increased. We usually use the same passwords on the internet and create simple passwords. By creating simple passwords, we can use our personel information, date of birth, place of birth and sequential numbers. Or the password of our debit cards and our e-mail password may be the same.
Using the same passwords for different accounts on the Internet causes a huge security vulnerability.Simple passwords can be estimated on the internet, through personal information shared on social media. Because if this password is learned in some way, it is possible that other accounts will be taken over by malicious people.
However, these passwords are easy to guess.
What is a strong password?
-These are passwords that are not easy to guess.
-They are passwords that are very difficult to get by trial and error.
So how to create a strong password?
– It should not consist of personal information and easily predictable information.
– Must be at least 8 characters.
– It must consist of letters, numbers and special characters.
– It must consist of uppercase and lowercase letters.
– Different passwords must be set for all accounts.
SOCIAL ENGINEERING
Babaeski Şehit Ersan Yenici AL. (Oya Arslan)
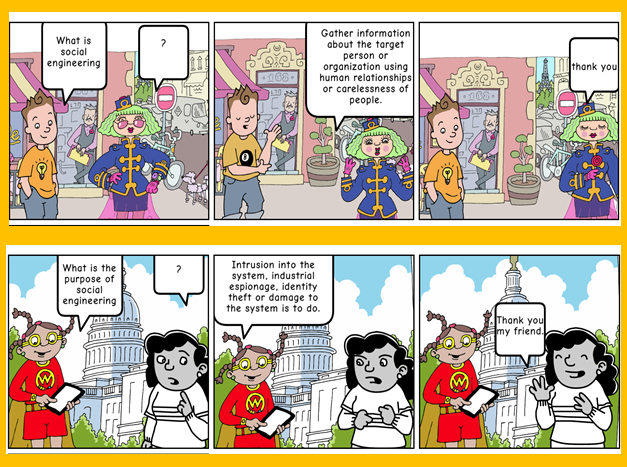
Social engineering is to try to obtain the desired information through various persuasion and deception methods by making use of the weaknesses of people on the Internet.
The social engineer follows some ways to deceive others.
It collects information about the victim and explores many features.
Plans the attack.
Determines the computer programs to use.
Uses the information collected.
What are the harms of social engineering attacks?
-Attackers can gain unauthorized access to the systems.
-It creates a loss of trust and reputation for the company or people.
-Data theft is done.
-The business processes of companies can be disrupted with the hijacked passwords or access information.
-Captured systems may become unavailable.
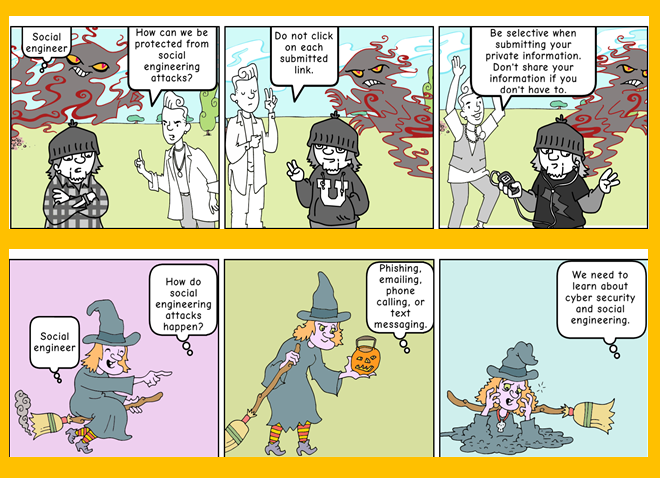
What are the measures that can be taken against social engineering attacks?
It should take security measures.
It is necessary to be aware of cyber attacks and to receive information security trainings.
Firewall and Antivirus are required to protect computers.
Callback method should be adopted against fake calls.
It is necessary to be skeptical about e-mail and SMS access.

RISKY ONLINE BEHAVIORS
Licee De Verlomme (Virginie Mathieu)
Who is at Risk?
With the advent of social networking sites and detailed chat profiles, predators don’t need to work very hard to piece together information about a child online. Predators can judge by the appearance of a profile or by the behavior that a child is exhibiting whether he or she might be a prime target for an online relationship.
Teens who don’t use privacy settings on social networking and gaming sites often place their information—including their deepest desires, likes and dislikes, real-time moods, pictures, addresses, and phone numbers—for anyone to see. Teens who post personal information, blog, or journal about sensitive issues may also be easy targets for predators who seek to isolate children from their parents and friends and exploit a child’s emotional vulnerabilities.
Risky online behaviors
The more risky behaviors kids engage in online, the more likely they will receive an online sexual solicitation.
These risky behaviors include:
1-Posting personal information (50%)
2-Interacting with online strangers (45%)
3-Placing strangers on buddy lists (35%)
4-Sending personal information to strangers (26%)
5-Visiting X-rated sites (13%)
6-Talking about sex with strangers (5%)

What is risky behaviour online?
Here’s a list of online actions that may have terrible outcomes, accompanied by the most common security threats they may pose.
1-Sharing everything with everybody.
*Checking in from every place you go to (including regularly checking in from the gym, favourite restaurant etc., thus creating a profile of yourself easily traceable by stalkers);
*Sharing photos taken with your phone (which are tagged with the exact location details of where the photo was taken);
*Sharing photos in funny situations (that can actually turn into compromising evidence of inappropriate behavior);
*Leaving your full birth date, phone number and home address on your public profile (for everyone to see, including ill-intended strangers);
*Discussing personal problems with friends and strangers through public comments.
2-Facebook in particular, have become the “school yard of cyberbullies”. It seems, take peer pressure at a whole new level: some teens may not only witness cyberbulling but they may actually join it. Similarly, seeing other “friends” having fun while drinking, they may develop a drinking behavior as well.
3-Ignoring privacy settings. Security and privacy threats: ruined online reputation, cyberstalkers, cyberbullies, child predators.
4-As a teen, lying about your age and setting dates with strangers offline. Offline threats: cyberstalkers, child predators.
5-Clicking on every link you come across. Internet security threats: malware infections, phishing sites.
6-Answering every quiz/survey that pops up. Internet security threats: phishing attempts, identity theft.
7-Falling for online freebie scams and making fake purchases. Or jumping at the opportunity. Internet security threats: malware infections, phishing sites.
8-Installing all sorts of apps (that collect information about you and share it with third-parties) without checking their developer first. Internet security threats: malware infections, identity theft.

What is safe behavior on Internet?
Here are rules to follow to ensure that a behavior that don’t put the security and privacy at risk of a person.
1-Do not friend total strangers.
2-For every photo, post, status you share on social networks, do the “granny test” and ask yourself: how would grandma feel about it? If you wouldn’t want her to see it, don’t post it.
3-Don’t share posts about you going on vacation. But do post about it when you’re back, if you want to.
4-Beware of Facebook malicious links to fake videos and photos posted by strangers. If they are accompanied by some outrageous news, event or celebrity gossip written in poor grammar, they may direct to phishing sites or start an automatic malware download. Also, links and photos shared by friends – they may have been infected with a Facebook “auto-sharing virus”.
5-Be careful with answering quizzes and surveys. Is it a site-sponsored quiz/survey? Who’s it run by? We may get caught up in a Facebook/Pinterest survey scam and fall victim to a phishing attempt.
6-Make sure you have proper internet security installed on your PC that comes with a Safe Browsing tool for Facebook.
7-Limit the number of Facebook apps we allow to use our personal information. We never know whose hands that information may end up in.
8-For every social media account created, it is necessary to choose a different password that has at least 8 characters, and includes numbers, upper case and lower case letters.
9-Always ask friends for permission to tag them in photos or check them in to places.
10-Check our online social exposure regularly – a simple “Google yourself” once in a while will do.



DIGITAL RIGHTS AND DIGITAL CITIZENSHIP
Keşan Ticaret ve Sanayi Odası MTAL (İlgi Dilmen)
In the age we are in, we use the internet and social media extensively.
It is important for individuals to know their rights and responsibilities in these environments.
Digital right refers to the freedom of individuals to access information, create content and publish the created content in digital media through computers and other electronic devices.
We leave digital footprints in all the work and transactions we do on the Internet. In this regard, we need to know our digital rights and what our responsibilities are.
We can classify our digital rights as follows:
*The right to privacy protection
*Rights to Privacy
*Freedom of Information
*Consumer Rights
Digital citizenship refers to the responsible use of technology by anyone who uses computers, the Internet, and digital devices to engage with society on any level.

This is why digital citizenship is such a crucial topic to teach today’s students.As the rate of technological advancement continues to increase, the world as a whole is becoming more dependent on the Internet for day-to-day activities.That can mean checking a bank account, purchasing a product, or simply keeping in touch with a friend.Regardless, the Internet is packed with potential pitfalls that could catch many students off-guard. More importantly, malicious Internet users can quickly harm someone online, even if it’s only through harsh words.
If you want to teach digital citizenship, you can focus seven key concepts to help students understand this broad concept:
1-Empathy
2-How the Internet works
3-Understanding user data
4-Practicing digital literacy
5-Acknowledging the digital divide
6-Practicing digital wellness
7-Securing digital devices



BACKUPS
IES Antonio Menárguez Costa (Laura Carrión)
Accidental deletion It is one of the most frequent causes of loss of information although it is not the unique, it can also be due to the action of a virus, the loss, failure or theft of the device (Smartphone, Tablet, Laptop, etc.)
Backups must be made since if you had not previously made copies security, your information will disappear, with what this means: losing memories and personal moments, repeating jobs to which you had dedicated time and effort, etc. The only safe way to retrieve information with certain guarantees is having a backup copy.
Tips and recommendations:
1) Select the information that under no circumstances would you like to lose.
2) Choose the media where you will store the information.
3) Make the backup duplicating the information in two or more supports. For example, one copy could be on an external hard drive and the other on the hard drive from laptop or even into a cloud service.
4) Repeat your copies periodically updating your copies to verify that it follows, on the one hand the available information, and on the other to include in these copies the new information that you have generated.

TIPS OF PARENTS WITH TEENAGERS
IES Antonio Menárguez Costa (Laura Carrión)
Parental supervision, support and guidance is essential to promote among minors the safe and responsible use of the Internet. One of the most effective ways to mediate in the children use on the Internet.
Some examples of how to do it:
– Know your children’s online friendships, the applications they use and their interests.
– Encourages the exchange of knowledge and experiences on the Internet, in this way they will find less difficulties when it comes to transferring your doubts and concerns.
– Share activities (eg to help you configure the privacy options of social networks, throw a game at an online game), is one of the best ways to monitor their activity in Internet and transfer new points of view with the intention of sensitizing them.
– Each thing has its time. Go adapting the rules and limits established according to age and trust that your children generate. Some online services, such as social networks, require some maturity for its use.
– Prevent access to inappropriate content by the minor.
– Limit the time of use of devices or certain types of applications.
– Prevent him from using certain vocabulary.
– Perform monitoring tasks to know the websites you have visited.



HIDDEN DANGERS IN SOCIAL NETWORKS AND
HOW TO USE IT SAFELY
Colegiul Dobrogean”Spiru Haret” (Aurelia Bazbanela)
When we talk about social networks, the first dangers we think of would be cyberbullying, which today is the main problem of social networks, but also sexual predators, which are beginning to appear more and more nowadays, due to the ease of pretending to be someone else or manipulating someone on the internet.
But before we start talking about other dangers that social networks pose, I think it would be good to highlight some benefits of the platforms.
Probably the first benefit that many would not have thought of when they started reading this article, would be that social networks create and gather friends or relationships. Now many of you may think that in general on social networks there are only predators and people who share “hate”, but let’s not forget that some people have met and made friends on these platforms or even got married, after they met on these platforms.
A second benefit would be that social networks are platforms on which many of us can promote their talents. In recent years, many artists, especially from the music industry, have been discovered on social platforms, such as Justin Bieber.
And the third benefit that deserves to be highlighted, would be that social networks are a place where you can learn things. On these platforms you can learn about music, photography, math, programming, but also how to cook or build certain objects and many other things.

Now that we have mentioned some advantages about social platforms and how they can be used productively, we must keep in mind that social platforms are also a big risk.
Probably the biggest danger, especially for children, is that people who use these platforms may be exposed to inappropriate or annoying content. Inappropriate content would be adult content. One study shows that one in nine teenagers receives sexually explicit messages or emails and at least one in seven teenegers sends such messages. The study also shows that more than 10 teenagers forward these messages to other people without their approval. But even more worrying is the fact that one in twelve young people resends these messages without the sender’s permission.
A second danger would be that when you start using social networks you start exposing too much of your personal life to the point where it becomes public.
A third danger would be that the use of social platforms reduces sleep duration. One study shows that one of ten young people say they always use social networks during the night. Lack of sleep is directly connected with loneliness, but also depression during adolescence.
A fourth danger would be that social networks can be a waste of time if you use them too much. A study shows that 44% of young people spend more than three hours a day on social networks.
And one last danger would be that in the long run the long-term use of social networks can lead to depression, anxiety and even suicidal thoughts.
So, given the dangers and benefits presented above, I think we can say that it depends on us, and those around us, how we use these platforms, these having both hidden benefits and dangers.

FORMS OF CYBER BULLYİNG
Gymnasium of Koroni, Greece (Gina Mouselimi)
1. Exclusion
Exclusion is the act of leaving someone out deliberately. For example, your child might be excluded/uninvited to groups or parties while they see other friends being included, or left out of message threads or conversations that involve mutual friends.
2. Harassment
Harassment is a broad category under which many types of cyberbullying fall into, but it generally refers to a sustained and constant pattern of hurtful or threatening online messages sent with the intention of doing harm to someone.
3. Outing/Doxing
Outing, also known as doxing, refers to the act of openly revealing sensitive or personal information about someone without their consent for purposes of embarrassing or humiliating them.
4. Trickery
Trickery is similar to outing, with an added element of deception. In these situations, the bully will befriend their target and lull them into a false sense of security. Once the bully has gained their target’s trust, they abuse that trust and share the victim’s secrets and private information to a third party or multiple third parties.
5. Cyberstalking
Cyberstalking is a particularly serious form of cyberbullying that can extend to threats of physical harm to the child being targeted. It can include monitoring, false accusations, threats, and is often accompanied by offline stalking.

6. Fraping
Fraping is when a bully uses your child’s social networking accounts to post inappropriate content with their name.
7. Masquerading
Masquerading happens when a bully creates a made up profile or identity online with the sole purpose of cyberbullying someone. This could involve creating a fake email account, fake social media profile, and selecting a new identity and photos to fool the victim
8. Dissing
Dissing refers to the act of a bully spreading cruel information about their target through public posts or private messages to either ruin their reputation or relationships with other people.
9. Trolling
Trolling is when a bully will seek out to intentionally upset others by posting inflammatory comments online
10. Flaming
This type of online bullying constitutes of posting about or directly sending insults and profanity to their target. Flaming is similar to trolling, but will usually be a more direct attack on a victim to incite them into online fights.

A ”get cyber skilled” scratch video.
It contains questions about cyberbullying.
Let’s scratch!
https://scratch.mit.edu/projects/376476940



PHISHING
CIP Tafalla (Eva Pérez)
Definition:
Acquire confidential information of victims by impersonating the identity of a legitimate source. The phenomenon has existed since the beginning of the Internet, but a situation such as the coronavirus pandemia can aggravate it.
The last known case of phishing has recently occurred. When the virus had only spread massively through China, the cybersecurity company Kaspersky alerted about emails that appeared to be arriving from the Centers for Disease Control and Prevention, offering prevention recommendations. To view them, users had to open a page, first entering the password of their emails. And that’s where the door opened for cybercriminals.
Another example has circulated on WhatsApp: if you wanted to buy an antivirus mask, you had to provide bank details.

DIGITAL FOOTPRINT
CIP Tafalla (Marian Úcar)
A digital footprint is a trail of data you create while using the Internet. It includes the websites you visit, emails you send, and information you submit to online services. There are two types of digital footprint:
1- A “passive digital footprint” is a data trail you unintentionally leave online. For example, when you visit a website, the web server may log your IP address, which identifies your Internet service provider and your approximate location. A more personal aspect of your passive digital footprint is your search history.
2- An “active digital footprint” includes data that you intentionally submit online. Since most people save their email online, the messages you send can easily remain online for several years or more.
Everyone who uses the Internet has a digital footprint, so it is not something to be worried about. However, it is wise to consider what trail of data you are leaving behind.
Once digital data has been shared online, there is no guarantee you will ever be able to remove it from the Internet.

CAUTIONS
Gjimnazi Rreshen (Velbona Reçi)
We human beings have a large history in our evolution and today in 2020 it is supposed that we have reached the peaks of humanity. In fact it’s complete the opposite because today we are facing more and more concerns than ever.
In 2020, with all that’s going on in the world, we are still picking and offending people smaller than us or people diffrent from us? And we call this humanity. In 2020 we are choosing bully as the best key word of our daily life and this is not being a human, is being a beast. In fact I haven’t seen animals acting with each-other like humans do, and at this point I would prefer better to be a cat or a dog than a human. We say the difference between us and those animals is exactly the reason we gave to all things we see and our behavior. Nowadays I’m not sure which is the creature who gives reason to everything, people or animals? Why I say this? Because there is no reason for us to disrespect our kind.
As Dave Willis said: ” Show recpect even to people who don’t deserve it, not as a reflections of their character but as a reflection of yours”. The worst thing is that we don’t do it neither with those who deserve it, nor with them that dont’t.
It’s okay to dislike someone, or even dislike someone for no reason, but it’s not okay to degrade and humiliate that person. Cyberbullying is killing people.
People who are bullying the others are those with a very low self-esteem and self-cofidence. In this way they try to be the best while offending the others. However, you will never look good trying to make someone else look bad, because blowing out someone elses candle, doesn’t make yours shine brighter.
You have no idea what I am dealing with in my personal life so just be nice, isn’t that simple? Why it’s necessary to say bad things about me only because you are insecure with yourself? Next time someone says something, remember it has nothing to do with you and everything to do with them. You may be normal and it’s okay but you may be weird as well and that’s okay too. So please don’t be blind and deaf in front of those who are disturbing you online and don’t let them break your heart .
BE NICE!






Published: May 23, 2020
Latest Revision: May 23, 2020
Ourboox Unique Identifier: OB-842287
Copyright © 2020








